¶ What is Engineering?
The concept of engineering is much larger than cybersecurity, and is really the practice of applying science and mathematics to solving problems. In the context of CIE this means process engineering, safety engineering, systems engineering, and yes, security engineering. But engineering, while being scientifically driven, which implies a rigorous process, also benefits from innovation in the pursuit of problem-solving. It is important that we adhere to a certain structure in design principles, but keep our options open to develop new and innovative problem-solving approaches as it makes sense, always staying within the boundaries of the core requirements of the project.
¶ Video Summary - Security Engineering in ICS
https://www.youtube.com/watch?v=ffhO6JuOAsA
¶ Comparing Engineering to Operations
The process of engineering culminates in a transition to operations, but engineering does not necessarily stop there as environments are dynamic, and as requirements change over time and changes occur inside the environment, it is common for systems redesign to occur, sometimes without proper planning, but nonetheless it is not always a clean cutover. We've tried to simplify the general definition of what activities are part of Security Engineering as opposed to Security Operations.
¶ Security Engineering
Focuses on designing and implementing security measures to protect systems and data from cyber threats.
- Typically involves planning, designing, and building security controls, systems, and infrastructure.
- Works to identify and mitigate security risks before they become a problem.
- Discrete activities may include:
- Conducting threat modeling and risk assessments
- Developing security architectures and designs
- Implementing encryption and access controls
- Configuring firewalls and intrusion detection/prevention systems
- Conducting security testing and validation
¶ Security Operations
Focuses on monitoring, detecting, and responding to security incidents in real-time.
- Typically involves managing and maintaining security tools and systems to detect and respond to threats.
- Works to contain and remediate security incidents as quickly as possible.
- Discrete activities may include:
- Monitoring security events and alerts
- Analyzing and investigating security incidents
- Managing and tuning security tools and systems
- Responding to security incidents and performing incident triage
- Conducting forensic investigations and analysis
In summary, security engineering focuses on designing and implementing security controls, while security operations focuses on monitoring and responding to security incidents. Both are critical components of a comprehensive cybersecurity program, and organizations should have both functions in place to ensure a strong security posture.
¶ Engineering Objectives
The practice of engineering really starts with a conceptual model of what the system will do, how it works, who the stakeholders are, and the inputs and outputs in the pursuit of solving a business problem. It's really not about the technology, but this is typically the output of the design engineering process so this is what we think of when we think of engineering. It requires a detailed set of requirements that dictate the parameters of the design, and ultimately a set of design deliverables that capture these requirements and mitigate the risks to the design. It is noteworthy that security by design principles are commonly not included, and as you can see in the engineering diagram below, there are very few places where any sort of assurance occurs until fairly late in the validation phases.
We will break up the primary sets of engineering activities into the following categories, but do not fixate on the order of the list, as all of these stages are part of the initial design.
- Process
- Safety
- Systems
- Security
¶ Engineering Process
As we look to understand the process of engineering, it is helpful to use lifecycle processes to structure our efforts. One of the most popular approaches is found within the Department of Transportation Systems Engineering process. It is commonly known as the DOT Vee, or the Engineering Vee as it follows a basic “V” shape and is shown below.
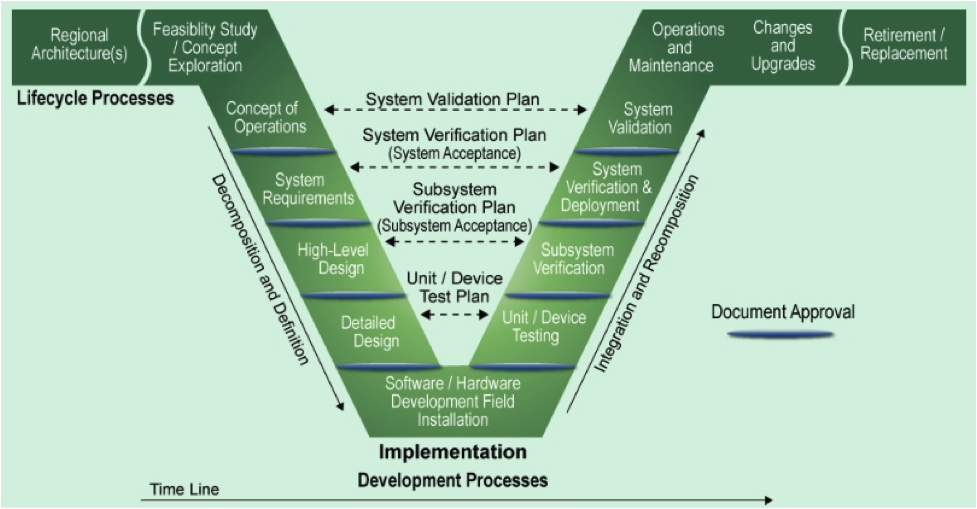
In this model, we start with the exploration of the concept of the problem that requires solving and start to flow down the left side of the V, starting with defining the Concept of Operations and flowing down until we begin development activities, and then flowing back up the right side of the V, using the latter activities as validation of the planning and design phases.
The Engineering Vee is a model used to describe the relationships between different phases of the system development life cycle. It emphasizes the importance of testing and verification throughout the system development life cycle, with a focus on early identification and resolution of any design or implementation issues. It also provides a clear structure for managing the system development process, with a logical progression from requirements analysis through to system verification.
This is a well-understood and popular approach, but for the sake of explanation, we will try to simply this even further into a 5 step process that summarizes the V.
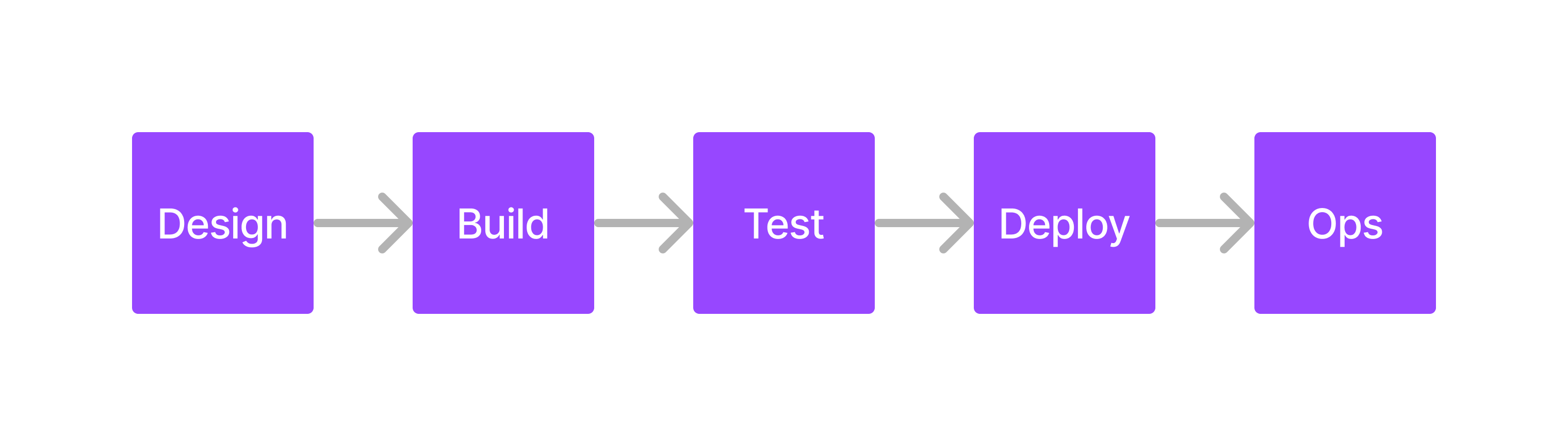
Now this is certainly an oversimplification, as there are a number of steps that are contained within each of these phases we will explore in more detail on subsequent articles as seen below, with a key difference being that we will weave in additional security activities that we feel should be included in these phases for maximum resilience:
¶ Resources
- Systems Engineering Body of Knowledge Wiki
- International Council on Systems Engineering (INCOSE)
- NIST 800-160 - Engineering Trustworthy Secure Systems
- Department of Transportation Systems Engineering Process
- ISA84, Instrumented Systems to Achieve Functional Safety in the Process Industries
- Cyber Resilient Weapons Systems Body of Knowledge (CRWS-BOK)
jjj