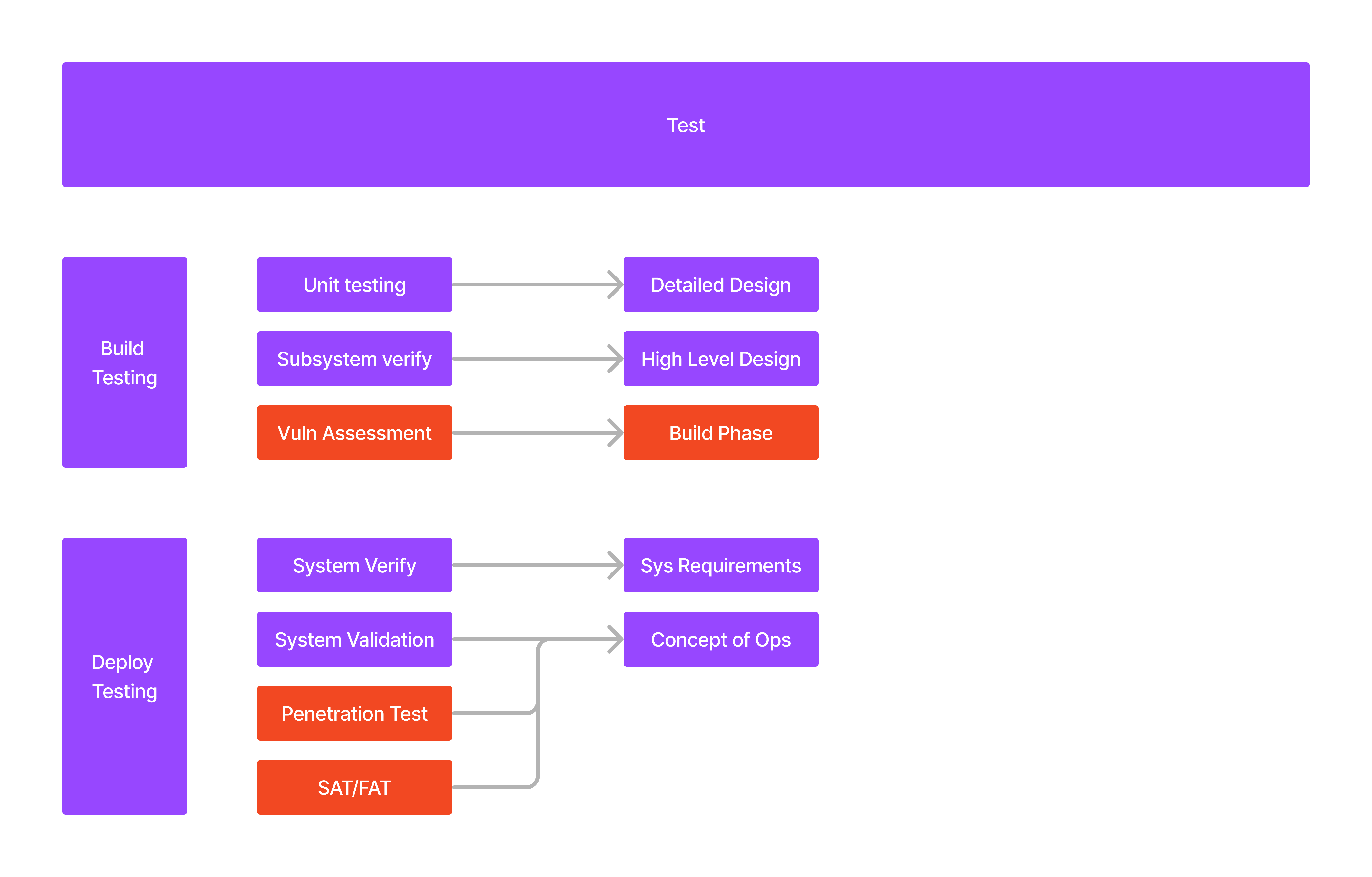
¶ What Activities are part of the Test Phase?
In testing phase, we are really performing verification and validation activities as a post build process. In the Engineering Vee, these discrete phases are really linked back to the predecessors they relate to, as such there is a direct linkage between testing phases to design and build phases we will try to describe below, but continuing our attempt at simplification of the process, and adding in additional security testing activities you can start to see how this all plays out.
Additionally, we have pushed some of these activites into the Deployment phase as they are really conducted after the system has been deployed into a production environment, as such as will break testing up into 2 sets of activities.
¶ Unit Testing
The Unit Testing phase is the stage of the system development process where individual units or components of the system are tested independently. The objective of Unit Testing is to verify that each unit or component meets its functional and performance requirements as defined in the system design.
Unit Testing is typically performed by the developers who have designed and implemented the individual units or components of the system. The activities in this phase typically include:
- Test Planning: Define the test objectives, test cases, and test procedures for each unit or component.
- Test Execution: Perform tests to verify the functionality and performance of each unit or component.
- Test Reporting: Record the test results, including any defects or issues found during testing.
- Unit Review: Review the unit design and the test results to ensure that each unit meets its functional and performance requirements.
The Unit Testing phase is critical because it ensures that each unit or component of the system meets its requirements and specifications before it is integrated into the larger system. By detecting and correcting defects early in the development process, Unit Testing helps to reduce the cost and time associated with debugging and testing the system as a whole. Additionally, by verifying the functionality and performance of each unit or component, Unit Testing helps to ensure that the overall system will function correctly and meet its technical requirements and specifications.
¶ Subsystem Verification
The Subsystem Verification phase is the stage of the system development process that follows the Component Integration phase. In this phase, each subsystem is tested to ensure that it meets the technical requirements and specifications defined in the system design.
The objective of the Subsystem Verification phase is to demonstrate that each subsystem functions correctly and meets the technical requirements and specifications when integrated into the larger system. The activities in this phase typically include:
- Test Planning: Define the test objectives, test cases, and test procedures for verifying each subsystem.
- Test Execution: Perform tests to verify each subsystem. These tests may include unit testing, integration testing, and subsystem testing.
- Test Reporting: Record the test results, including any defects or issues found during testing.
- Subsystem Review: Review the subsystem design and the test results to ensure that each subsystem meets the technical requirements and specifications.
- Component Integration: Integrate the subsystem components into the larger system to ensure that they function correctly when working together.
The Subsystem Verification phase is critical because it ensures that each subsystem functions correctly and meets the technical requirements and specifications when integrated into the larger system. It is also an opportunity to identify and correct any defects or issues before the system is moved to the System Verification phase, which is the next stage of the system development process. By completing the Subsystem Verification phase, each subsystem is ready for testing in the System Verification phase to ensure that the overall system meets the technical requirements and specifications.
¶ Vulnerability Assessment
A vulnerability assessment is the process of identifying and evaluating vulnerabilities, weaknesses, and potential threats within a system, network, or application. The objective of a vulnerability assessment is to identify security weaknesses that can be exploited by malicious actors to gain unauthorized access to or compromise the confidentiality, integrity, or availability of a system.
The vulnerability assessment process typically involves the following steps:
- Identification of assets: Identify the assets and resources that need to be protected, such as servers, databases, applications, and network devices.
- Threat modeling: Identify the potential threats and attack vectors that can be used to exploit the vulnerabilities of the system.
- Vulnerability scanning: Perform an automated scan of the system using specialized tools to identify known vulnerabilities.
- Manual testing: Conduct manual testing to identify vulnerabilities that cannot be detected by automated scanning tools.
- Risk assessment: Evaluate the identified vulnerabilities and prioritize them based on their potential impact on the system and the likelihood of exploitation.
- Reporting: Generate a report that documents the identified vulnerabilities, the potential risks, and recommendations for remediation.
The results of a vulnerability assessment can be used to improve the security posture of the system by identifying and addressing security weaknesses and implementing appropriate controls to mitigate the risks. Regular vulnerability assessments are essential to maintain the security of a system, as new vulnerabilities are discovered all the time, and attackers are constantly looking for new ways to exploit them.
¶ System Verification
The System Verification phase is the stage of the system development process that follows the System Integration phase. In this phase, the system is tested to ensure that it meets the technical requirements and specifications defined in the system design.
The objective of the System Verification phase is to demonstrate that the system design is complete and accurate and that the system components function correctly when integrated into the larger system. The activities in this phase typically include:
- Test Planning: Define the test objectives, test cases, and test procedures for verifying the system.
- Test Execution: Perform tests to verify the system. These tests may include unit testing, integration testing, and system testing.
- Test Reporting: Record the test results, including any defects or issues found during testing.
- System Review: Review the system design and the test results to ensure that the system meets the technical requirements and specifications.
- System Integration: Integrate the system components into the larger system to ensure that they function correctly when working together.
The System Verification phase is critical because it ensures that the system components are working correctly and that they are integrated correctly into the larger system. It is also an opportunity to identify and correct any defects or issues before the system is moved to the System Validation phase, which is the final stage of the system development process. By completing the System Verification phase, the system is ready for testing in the System Validation phase to ensure that it meets the user requirements and is ready for deployment.
¶ System Validation
The System Validation phase is the final stage of the system development process. In this phase, the system is tested to ensure that it meets the user requirements and is ready for deployment. The objective of this phase is to demonstrate that the system performs as expected and meets the specified requirements.
The activities in the System Validation phase typically include:
- Test Planning: Define the test objectives, test cases, and test procedures for validating the system.
- Test Execution: Perform tests to validate the system. These tests may include functional testing, performance testing, stress testing, and user acceptance testing.
- Test Reporting: Record the test results, including any defects or issues found during testing.
- System Acceptance: Obtain acceptance from the customer or end-user that the system meets their requirements and is ready for deployment.
- System Deployment: Deploy the system into its production environment.
The System Validation phase is critical because it ensures that the system meets the user requirements and performs as expected. It is also the last opportunity to identify and correct any defects or issues before the system is deployed. By completing the System Validation phase, the system development process is completed, and the system is ready to be used by its intended users.
¶ Penetration Test
A penetration test, also known as a pen test, is a simulated cyber attack against a computer system, network, application, or other digital asset, conducted by security professionals to identify vulnerabilities that could be exploited by real attackers. The goal of a penetration test is to simulate a real-world attack scenario and determine the effectiveness of the organization's security controls in detecting and preventing such attacks.
Penetration tests typically involve the use of various tools and techniques to attempt to exploit vulnerabilities in the target system or network. These tests can be performed either internally by security professionals within the organization or externally by third-party security firms.
Penetration tests can be categorized into different types based on their scope and level of access granted to the testers. Some common types of penetration tests include:
- Black-box testing: Testers are not given any prior information about the target system or network and must conduct the test as if they were a real attacker.
- White-box testing: Testers are given full knowledge of the target system or network, including source code and network diagrams, to simulate an insider attack.
- Gray-box testing: Testers are given partial information about the target system or network, such as login credentials or network topology, to simulate an attack from a trusted insider or external attacker who has some level of knowledge about the target.
- Physical penetration testing: Testers attempt to gain physical access to the target system or network, such as breaking into a facility or stealing a device, to simulate a real-world attack scenario.
Once the penetration test is complete, the security professionals will provide a report that details the vulnerabilities and weaknesses that were identified and recommendations for improving the security of the target system or network. This information can be used by the organization to prioritize security improvements and strengthen its overall security posture.
¶ Site Acceptance Test
A Site Acceptance Test (SAT) is a type of test that is conducted to verify that a system or equipment meets the acceptance criteria and specifications that have been agreed upon between the customer and the vendor. The SAT is usually performed on-site at the customer's location, and it involves a set of tests that are designed to simulate real-world operating conditions.
During the SAT, the customer's representatives typically observe the testing process and verify that the system or equipment meets the agreed-upon specifications. The tests that are performed during the SAT may include functional testing, performance testing, safety testing, and environmental testing. The testing process is usually documented, and the results are reviewed and approved by both the customer and the vendor.
The SAT is an important step in the process of deploying a new system or equipment, as it provides assurance that the system or equipment is operating as intended and meets the requirements of the customer. It also helps to identify any issues or problems that need to be addressed before the system or equipment is put into service. Once the SAT is successfully completed, the system or equipment can be accepted by the customer and put into operation.
¶ Facility Acceptance Test
A Facility Acceptance Test (FAT) is a type of test that is conducted to verify that a newly constructed or modified facility meets the requirements and specifications that were agreed upon between the customer and the contractor. The FAT is usually performed on-site at the facility, and it involves a set of tests that are designed to simulate real-world operating conditions.
During the FAT, the customer's representatives typically observe the testing process and verify that the facility meets the agreed-upon specifications. The tests that are performed during the FAT may include functional testing of equipment and systems, testing of safety systems, testing of environmental controls, and testing of utility systems. The testing process is usually documented, and the results are reviewed and approved by both the customer and the contractor.
The FAT is an important step in the process of commissioning a new facility, as it provides assurance that the facility is operating as intended and meets the requirements of the customer. It also helps to identify any issues or problems that need to be addressed before the facility is put into service. Once the FAT is successfully completed, the facility can be accepted by the customer and put into operation.