¶ What is Interdependency Evaluation?
Systems are complex and interconnected. There are multiple stakeholders both internally and externally, and the relationship between upstream and downstream systems, their dependencies and related critical infrastructure sectors creates a house of cards where even a single failure can have cascading consequences. Similarly, the intersection of operations, automation engineering, cybersecurity and other business stakeholders creates opportunities for decisions to be made in a vacuum without all of the facts, leading to poor outcomes. For these reasons, the concepts behind interdependency evaluation necessitates a holistic view of the engineering and operations decisions to be made.
To put it simply, interdependency evaluation is about talking to people, and including them in the process.
¶ Video Summary - Interdependency Evaluation
https://www.youtube.com/watch?v=pLFSMTkn1xQ
¶ Why is it Important?
In 2015, Argonne National Laboratory conducted a study titled Analysis of Critical Infrastructure Dependencies and Interdependencies where they broke down the concept of dependencies and interdependencies in the domains of physical, cyber, geographic and logical and further broke them up into upstream, internal and downstream.
Below you can see a graphic depicting the interrelationship with multiple critical infrastructure sectors. For instance, in many regions of the world, gas pipelines provide a significant amount of fuel to produce electric power. The pipelines are not subject to NERC CIP regulations, and electric power operators that rely on this gas to produce power may be operating under a different set of critical infrastructure protections, inconsistent with the assumptions they have made in their own design. And communications infrastructure outages may produce cascading effects across many sectors that rely on site to site, or site to field communications to carry out their normal functions.
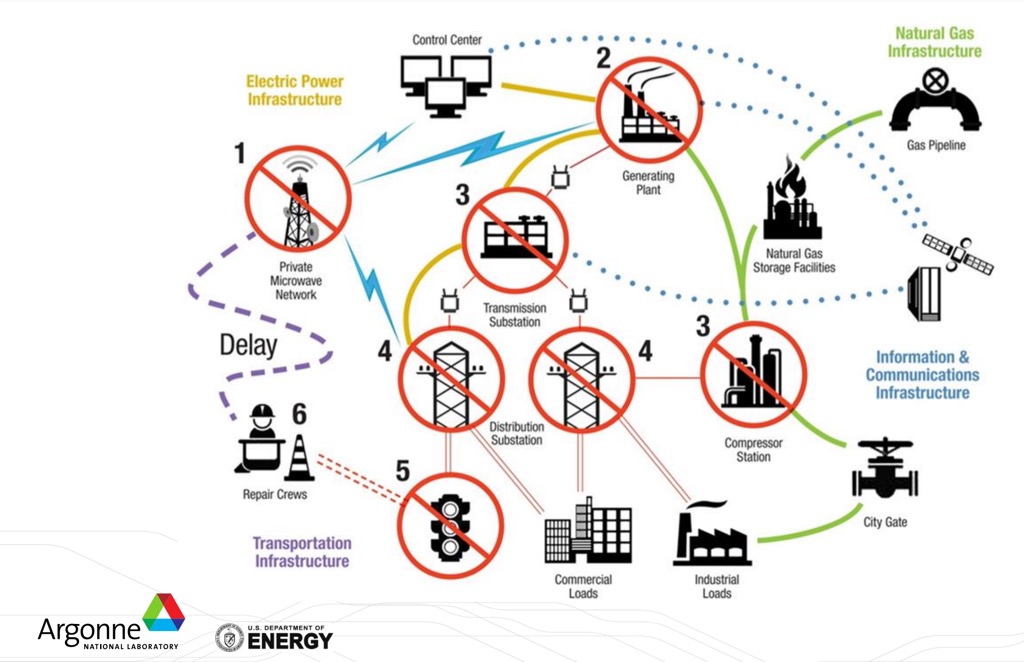
Retrieved from a presentation by Frédéric Petit and Lawrence Paul Lewis of Argonne National Laboratory
As we explore the interrelationships between our critical functions and their dependencies, its important to understand the different types of dependencies that emerge. As it relates to Cyber Informed Engineering, and specifically Consequences-driven Cyber-Informed Engineering, there are 3 common areas that emerge that are frequently targeted by adversaries that have the potential to create impact for us.
- Physical infrastructure choke points - If you rely on a pipeline or transmission line, or some other physical infrastructure to deliver your critical function, the attacker does not need to directly attack you. Especially of those upstream dependencies are not as stringently protected, it may make far more sense to target upstream, as not only will it create impact for you, but if there are other downstream organizations that also rely on that infrastructure, the attack becomes far more valuable. This is essentially how supply chain attacks work as well.
- Horizontal application of technology - Widespread adoption of technologies such as DNS or specific ICS protocols creates an over-reliance on services that may have little redundancy in place unless you have designed for it. If the compromise of a specific OEM creates an outage in your infrastructure, it may be very challenging to recover as replacement is not quick or easy, and reovery might be a long time coming, especially if that vendor is suffering major consequences themselves. The move towards standardization creates major scalability benefits, and can also simplify design and make our human resources far more capable of managing the environment.
- Reliance on Automation - As we have grown and become more digitized, we justify the investments with a reduction in labor. But what happens when the people are no longer there and the automation fails? It can be challenging to return to manual operations. Its important as we modernize our capabilities that we engineer in planned failure and have a plan to fail gracefully in the absence of digital control. Additionally, with hyper-automation and AI, the potential for an adversary to taint the data and logic of the AI means that direct attacks on our infrastructure might no longer be necessary to achieve their desired result.
There is one more set of dependencies that we need to be cognizant of. That is the people that do the work. Our critical functions are dependent on people, process and technology. We need infrastructure, data and systems to support the process. The process should be well-defined as wel implement our systems, and typically this is much better understood in OT as opposed to IT where we do not have as much human generated change and variability on context. But if the humans themselves are unavailable due to sickness or injury, or are performing other work, then the process may fail just from a lack of attention.
One of the most effective ways to obtain this level of understanding in dependency relationships is the concept of a Business Impact Analysis, or BIA. This is a key deliverable when standing up a business continuity, or continuity of operations plan. It's also closely related to the analysis performed by a PHA style assessment. We will cover these assessment types exhaustively in a future article on Consequences-Focused Design.
A BIA is a process that assesses the potential impact of various threats and disruptions to an organization's critical business operations, processes, and assets. The BIA identifies the critical business functions, the resources required to support those functions, and the potential impacts of disruptions to those resources. The process involves analyzing various scenarios, such as natural disasters, cyberattacks, or supply chain disruptions, and evaluating the potential impact on the organization's financial, operational, and reputational aspects. The BIA helps organizations prioritize their resources and efforts towards mitigating and recovering from the most critical threats to minimize the impact of such incidents. The outcome of the BIA provides a basis for developing and implementing effective continuity and recovery plans, ensuring that the organization can maintain essential services and operations in the face of unexpected events.
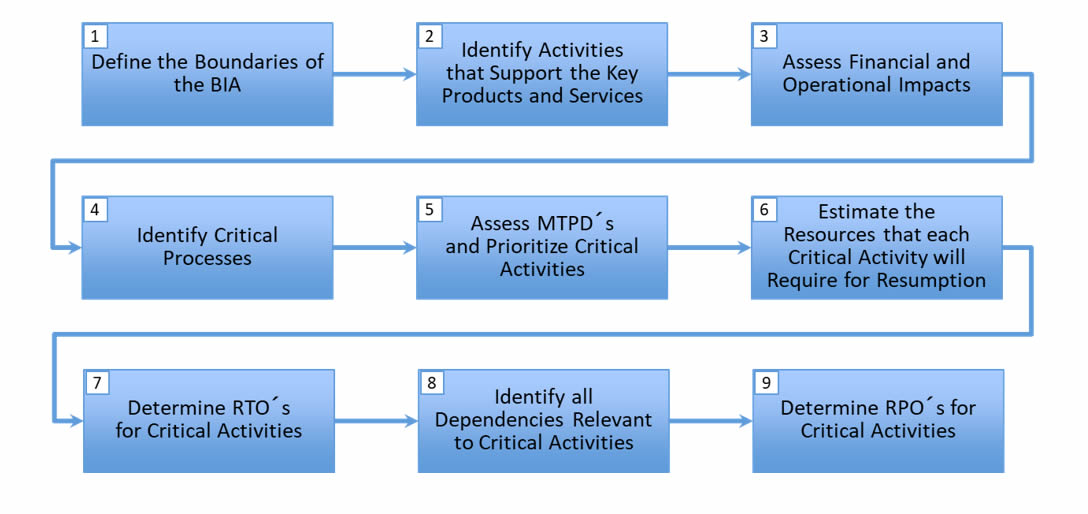
¶ Sector
Frequently we take a sector-specific view on critical infrastructure protection. After all, each sector has unique challenges, operating authority and even legal structures at the state and federal level. In some cases this works well, in others, such as municipalities and entities such as airports that operate as a pseudo municipality with their own power, water, gas, emergency services and building management infrastructures, this interconnect creates major complications for regulatory control and understanding of security requirements. But it certainly makes the topic of interdependency evaluation easier since there are fewer stakeholders to coordinate.
The 16 Critical Infrastructure sectors as defined by CISA within the United States (your country may define different sectors):
- Chemical - DHS was identified as the Chemical Sector Risk Management Agency (SRMA) in Presidential Policy Directive (PPD) 21. CISA performs the Chemical Sector SRMA responsibilities on behalf of DHS. CISA leads the Chemical Sector’s public-private partnership and works with companies to develop tools and resources that enhance the sector’s security and resilience.
- Commercial Facilities - The Commercial Facilities Sector protects spaces open to the general public against coordinated attacks. CISA offers strategic direction across eight subsectors to improve security and resilience in these locations.
- Communications - The communications sector has evolved into a complex industry of terrestrial, satellite, and wireless systems with many interdependencies. CISA works with private sector stakeholders to implement the risk management framework to protect all aspects of the communication sector.
- Critical Manufacturing - CISA identifies, assesses, prioritizes, and protects manufacturing industries with national significance to prevent and mitigate the impact of manmade or natural disasters.
- Dams - With more than 90,000 dams in the U.S., the Dams Sector delivers critical water retention and control services. CISA works with sector partners to protect assets from natural disasters, as well as human-caused and technological events.
- Defense Industrial Base - Over 100,000 companies and subtractors supply materials, services, and facilities to the U.S. military. The Defense Industrial Base Sector helps mobilize, deploy, and sustain these military operations around the world.
- Emergency Services - Supporting millions of skilled personnel with physical and cyber resources, the Emergency Services Sector helps save lives, protect property and the environment, and assist in recovery efforts after emergencies and disasters.
- Energy - The energy sector protects a multifaceted web of electricity, oil, and natural gas resources and assets to maintain steady energy supplies and ensure the overall health and wellness of the nation.
- Financial Services - By protecting financial institutions of all sizes from large-scale power outages, natural disasters, and cyber-attacks, the Financial Services Sector protects your financial assets as well as your ability to access and utilize those assets.
- Food and Agriculture - The food and agriculture sector, including farms, restaurants, and food manufacturing, processing, and storage facilities, is almost entirely privately-owned. CISA provides guidance, resources, and collaboration with interdependent sectors to protect against a range of risks.
- Government Facilities - Federal, state, local and tribunal government buildings and spaces have differing accessibility restrictions and purposes. The Government Facilities Sector helps these facilities identify their unique risk factors and protect against potential attacks or issues.
- Healthcare and Public Health - The Healthcare and Public Health Sector focuses on population health and provides the response and recovery actions needed after large-scale hazards such as terrorism, infection disease, and natural disasters.
- Information Technology - The nation’s growing dependency on information technology has made the Information Technology Sector mission – to identify and protect against cyber threats and vulnerabilities— more complex and important in the 21st century.
- Nuclear Reactors, Materials and Waste - From the power reactors that provide electricity to millions of Americans, to the medical isotopes used to treat cancer patients, America has an extensive civilian nuclear infrastructure.
- Transportation Systems - Moving millions of people and goods across the country every day, the transportation systems sector is exposed to a limitless number of threats and risks. CISA works to protect these systems and ensure a continuity of operations.
- Water and Wastewater - Access to clean, healthy water is a requirement for all human activity. Protecting the systems that provide water is of vital importance to the stability and health of the nation and is the mission of the Water and Wastewater Systems Sector.
At the sector level, it important to understand who your stakeholders are to understand the following areas. It's also important that you understand if somebody in your organization has already been tasked with these responsibilities so you don't “cross signals”:
- Legal Authority - For every jurisdiction that you are operating under, who are the entities that govern laws at the local, state and federal levels? Do you have a point of contact externally or is there an internal legal department that handles these questions?
- Professional Engineering Associations - For your sector and area of responsibility, what organizations govern acceptable engineering practices? Are there different expectations for different kinds of projects? Do you know what these are and who to ask if questions arise?
- Regulatory Control - Is your sector subject to any regulatory requirements? What are they? make sure these are included in the compliance requirements for your engineering project, certainly, but it may be necessary to reach out to an authority with any questions you might have.
- Public-Private Partnerships - is there an entity that is handling Public-private partnerships for your sector? This is a role that CISA commonly plays, but if there are other organizations that are helping to facilitate this conversation, you should be aware of them and
- Trade Organizations - these entities tend to be sector specific and even subsector specific such as an organization focused on transmission operators in electric power. They provide resources for their members and often advocate in industry for the collective needs of them.
- Incident Reporting - Do you know where incidents are reported, or what security resources are available? This may differ based on which sectorI(s) you organization supports, or you might only work with centralized critical infrastructure organizations such as CISA.
- Cross-sector coordination - Do you have somebody responsible for cross-sector coordination? Your project might only influence a pipeline or telecommunications and your sector contacts might be sufficient, but what about multi-sector impacts? How are you handling the conversation with multiple stakeholders?
A list of common stakeholder organizations can be found at Organizations.
¶ Organization
At an organizational level, this bleeds over into the concept of supply chain. Our organization has upstream and downstream suppliers, but it's not just software or accounting services, but the infrastructure we rely on. Even within a given sector, for instance an electric power operator may work with many different power generation, transmission or distribution to ultimately produce the service that their downstream customers rely on. These dependencies can present a challenge if we do not have resiliency to fail over to alternate providers, or if that dependency creates a conduit for the attacker to intrude upon your network.
We will cover the topics involved with Cyber Secure Supply Chain Controls in a separate article, but we do want to make the point here that in your engineering design process, these dependencies must be mapped out, and you need to know who to call when an issue occurs. Too often we have seen scenarios where an incident occurred and nobody knew who to call to get it resolved, or the normal recipient was unavailable. External stakeholders absolutely need to be part of your continuity of operations and disaster recovery exercises.
Some of the more common external parties we see include:
- Engineering, Procurement and Construction (EPC) - a firm that provides a comprehensive range of services to design, build, and deliver large-scale industrial and infrastructure projects. EPC companies manage the entire project lifecycle, from initial concept and design through procurement of materials and equipment, construction, commissioning, and handover to the owner. By consolidating responsibility for all aspects of the project under one entity, the EPC approach streamlines project management, increases efficiency, and minimizes risks associated with cost overruns, scheduling delays, and quality issues. EPC companies operate in various sectors, including oil and gas, power generation, transportation, and water treatment.
- Main Automation Contractor (MAC) - A specialized engineering firm or systems integrator responsible for designing, implementing, and managing the automation and control systems for large-scale industrial projects. They serve as a single point of contact for the project owner, coordinating the efforts of various equipment vendors, subcontractors, and engineering teams to ensure seamless integration and functionality of the automation system. The MAC approach simplifies project management, improves communication, and reduces the risk of delays or budget overruns by consolidating responsibility for the entire automation scope under one entity. This approach is commonly employed in industries such as oil and gas, chemical, power generation, and manufacturing.
- System Integrators - a company or engineering firm that specializes in bringing together various subsystems, components, and technologies to create a cohesive, functional, and efficient system for their clients. System integrators have expertise in multiple domains, such as automation, control systems, software, and hardware. They work closely with product vendors, suppliers, and end-users to design, configure, and implement solutions tailored to specific industry needs or project requirements. By integrating diverse technologies and components into a unified system, system integrators play a vital role in ensuring seamless operation, improving efficiency, and enhancing the overall performance of industrial facilities, infrastructure projects, and other complex systems.
- Consulting firms - provide specialized expertise and advisory services to help clients design, implement, and optimize their infrastructure and systems. They assist in areas such as risk assessment, cybersecurity, regulatory compliance, asset management, and process optimization. These firms collaborate with project stakeholders, including EPC companies, system integrators, and product vendors, to ensure the successful execution of projects while adhering to safety, environmental, and operational standards. By offering strategic guidance, technical know-how, and best practices, consulting firms play a crucial role in enhancing the resilience, efficiency, and performance of critical infrastructure and industrial facilities, ultimately helping organizations meet their goals and address challenges in a rapidly evolving landscape.
- Product Suppliers - a company that manufactures, distributes, or sells components, equipment, or materials. These companies specialize in producing specific products or product lines, such as electrical equipment, instrumentation, software, or industrial machinery. Product vendors or suppliers play a crucial role in the supply chain, working with engineering firms, contractors, system integrators, and end-users to provide the necessary components for the construction, operation, and maintenance of industrial facilities, infrastructure, or consumer goods. Their expertise in their respective product domains ensures that customers receive high-quality, reliable, and cost-effective solutions tailored to their specific needs and requirements.
- Upstream service providers - a company or entity responsible for the initial stages of resource extraction, production, or generation, which is vital for the functioning of downstream operations. Examples include upstream oil and natural gas companies involved in exploration, drilling, and extraction, power generation entities such as power plants producing electricity from various sources, and water management organizations responsible for securing and managing water sources like rivers, reservoirs, or wells. These upstream providers are essential to maintaining the steady supply of resources or services that downstream operators, such as refineries, utility companies, or water treatment plants, rely on to deliver critical services and products to end-users, ensuring the stability and resilience of the overall infrastructure system.
¶ Business Unit
You may have dependencies within your organization that are not immediately clear. For instance, the public news articles around the Colonial Ransomwre attack, suggested that the pipeline was shutdown not because of a direct impact to the ICS, but because the billing system was disabled due to ransomware. Without the ability meter and bill downstream customers, the decision was made to shutdown the pipeline. Is this a scenario where an offline capture of this information in an isolated state might make sense so that live connection failures do not create business interruptions? That is a conversation for Colonial, as ultimately it comes down to a risk management call.
You should be having similar conversations in your own organization to determine the traceability of dependencies. In many cases, this activity could be conducted in parallel with business continuity exercises, or using business impact analysis assessment as inputs to determine those key dependencies. Additionally, different forms of process hazards analysis (PHA) can be used as well. Both of these concepts are covered exhaustively in the Consequence-focused Design section, but these inputs are especially relevant for dependency and interdependency evaluation.
Some common areas of the business that have a need to engage with project teams might include:
- Finance - Financial planning, management, and oversight are critical for ensuring that the project is economically viable, properly funded, and executed within budget constraints. This involves securing funding from investors, lenders, or public sources, managing cash flow, conducting cost-benefit analyses, and monitoring project expenses. Additionally, financial teams collaborate with project stakeholders to assess and mitigate financial risks, such as cost overruns, currency fluctuations, or market volatility. They also ensure compliance with relevant financial regulations, taxes, and reporting requirements.
- Procurement - sourcing, acquiring, and managing the necessary materials, equipment, services, and resources required for the successful execution of the project. This involves identifying and selecting suitable suppliers, vendors, or contractors, negotiating contracts and pricing, managing the logistics of supply and delivery, and ensuring the quality and timely delivery of goods and services. Procurement teams work closely with project managers, engineers, and other stakeholders to balance cost, quality, and schedule considerations while mitigating risks such as supply chain disruptions, supplier performance issues, or cost overruns.
- Operations - management, control, and maintenance of the infrastructure system or facility, ensuring its safe, efficient, and reliable functioning. This includes overseeing the day-to-day activities of the facility, monitoring system performance, optimizing processes, implementing standard operating procedures, and ensuring compliance with safety, environmental, and regulatory requirements. Operations teams work closely with engineers, technicians, and other stakeholders to maintain system resilience, troubleshoot issues, and plan for upgrades, expansions, or modifications as needed. They also collaborate with external entities, such as utility providers, regulators, or emergency services, to coordinate and manage interconnected systems and respond to incidents or disruptions.
- Cybersecurity - protection of the digital systems, networks, and data that support the operation, control, and management of the infrastructure. Cybersecurity measures aim to prevent unauthorized access, data breaches, and other cyber threats that could compromise the safety, reliability, and performance of critical infrastructure systems. This involves implementing a combination of technical, procedural, and physical controls, such as firewalls, intrusion detection systems, encryption, access control policies, and employee training. Cybersecurity teams work closely with engineers, operations staff, and other stakeholders to assess and mitigate risks, monitor for potential threats, and respond to incidents.
- Enterprise Risk Management (ERM) - a holistic approach to identifying, assessing, and managing the various risks that can impact the project's objectives, operations, and overall success. ERM encompasses a wide range of risks, such as financial, operational, technological, regulatory, environmental, and reputational risks. The goal is to develop a comprehensive understanding of the risk landscape, prioritize risks based on their potential impact and likelihood, and implement appropriate mitigation strategies to minimize negative outcomes. ERM teams work closely with project managers, engineers, operations staff, and other stakeholders to establish a robust risk management framework that includes risk identification, assessment, monitoring, reporting, and control measures. This collaborative approach ensures that risks are proactively managed and that the organization is prepared to respond effectively to unforeseen events or changing conditions.
- Safety - focuses on implementing proactive measures to protect the well-being of employees, the public, and the environment, as well as preventing accidents, incidents, or damage to the infrastructure system. The safety business unit conducts various activities, such as identifying hazards, assessing risks, and establishing safety controls and procedures, including personal protective equipment, safety training, and emergency response plans. Collaboration among project managers, engineers, operations staff, and other stakeholders is essential for fostering a safety culture and ensuring adherence to relevant safety standards, regulations, and best practices.
- Compliance - ensure adherence to relevant laws, regulations, standards, and best practices governing the project's design, construction, operation, and maintenance. The department collaborates with project managers, engineers, operations staff, and other stakeholders to establish and maintain a robust compliance framework. This includes monitoring regulatory changes, conducting audits and assessments, providing guidance on compliance matters, and implementing corrective actions when necessary. By effectively managing compliance, the department helps minimize legal, financial, and reputational risks, ensures the long-term sustainability of the infrastructure, and maintains the safety, security, and performance of the system in accordance with regulatory expectations.
- Legal - collaborates with project managers, engineers, operations staff, and other stakeholders to identify and mitigate legal risks throughout the project lifecycle. This includes reviewing contracts, identifying and managing potential liability risks, providing legal guidance on issues such as intellectual property, employment law, and environmental compliance, and representing the organization in legal disputes or negotiations.
¶ Discipline
When engaged in engineering decisions, its important to note that no single person in the room has all the answers. Most of us are highly specialized in our tasks, and its important to note that there may be an exhaustive set of requirements for the engineering project that span functional, compliance and security requirements and cross multiple domains of expertise. In 2022, the Security Energy Infrastructure Executive Task Force (SEI ETF) project created a number of site profiles and reference architectures for electric power that included a list of parties that are frequently involved with the engineering and operation of an industrial control system environment. There may be other stakeholders such as chemical experts or other safety engineers, but this list should be enough to get you started in understand who the players are that we need perspective from when designing our system to prepare for operational dependencies.
- OT Manager
- Engineer
- Relay Technician
- Field Service Technician
- Solar/Wind/Hydro Operator
- Operations and maintenance
- SCADA
- EMS Support
- Cybersecurity
- Remote Employees
- Vendors
- 3rd Party Service Providers
- IT Services
- IT Manager
- Business Planning
One last point, every one of these people, organizations, etc has their own set of priorities. As part of this effort, you need to make sure you are all rowing in the same direction, or at least know where opportunities for conflict exists so you can plan accordingly.
For instance, product suppliers want to sell product, consultants want to sell services, you might be jockeying for a promotion or maybe you just want to make it home in time for dinner tonight. Maybe one department gets bonuses based on system uptime, while cyber is incentivized based on time to detect a cyber incident. But its important to recognize the motivations of each stakeholder and understand that you may be incentivized by very different things.
¶ How do we do it?
The first step is identifying who the entities are that we need to engage with. If you look at the Engineering Vee - you will notice that the Concept of Operations in the Design phase includes Stakeholder identification as one of the very first activities in the process. This is the stage where we identify what it is we are building, and how it will be used operationally, and also includes a very high level set of requirements. This is a great starting point to determine who else needs to be involved in the conversation.
As we get deeper into the design process with detailed design and threat modeling activities, you will naturally identify additional dependencies and new stakeholders to be included. That's OK, add them to the list and make sure to engage with them.
On this page we highlighted the BIA process and pointed out that PHA can be very effective in gaining the understanding needed to start to do this. But you also need toi document your process and formlize the engagement model with these stakeholders. They should be involved in the conversation and the key decision point, and even if they do not have the authority, the goodwill you buy involving them will result in increased cooperation once issues occur later.
¶ When do we do it?
This activity needs to start as soon as you know you have a project. This is not a once and done thing, and you can;t wait too long, as once decisions are made you may alienate the people you did not include in the conversation. Similarly, without their feedback, you will miss valuable inputs into the design process.
An engineering project is a living, breathing entity, that grows over time. While it does have a finite end point, the business is ever-evolving and you will need constant check and readjust phases even after the project concludes. We talk about the need for user acceptance and retrospectives in the Engineering Basics article, and this is an ongoing activity.
¶ What resources can help?
This is not a capability you can completely buy, per se. It requires some work to identify stakeholders, develop the process and execute it. But there are workflow automation tools available to support this process. Some organizations choose to develop their own using Sharepoint or other methods. Some choose to use SaaS project and task management tools to simplify this process. A few common ones are listed below, with free and paid options and include:
And new breeds of engineering workflow tools are starting to emerge such as the Opswright Impact platform that is developed by the team responsible for this wiki. We've designed the solution based on the concepts documented here, but it is by no means the only way to accomplish these tasks. Bottom line, use what works for you, perhaps you already have workflow and stakeholder coordination tools inside your organization today.